Take a look at the terms “information policies,” “information procedures,” “information standards,” and “information guidelines.” Aren’t these basically the same thing?
No, they are not and here’s why.
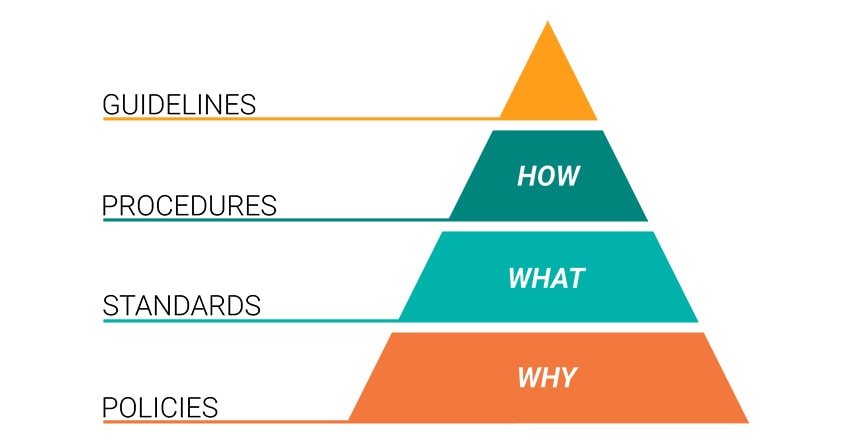
Policy
Policies are formal statements produced and supported by senior management.
They can be organization-wide, issue-specific, or system-specific. Your organization’s policies should reflect your objectives for your information security program—protecting information, risk management, and infrastructure security. Your policies should be like a building foundation; built to last and resistant to change or erosion.
- Driven by business objectives and convey the amount of risk senior management is willing to accept.
- Easily accessible and understood by the intended reader
- Created with the intent to be in place for several years and regularly reviewed with approved changes made as needed.
Standard
Standards are mandatory courses of action or rules that give formal policies support and direction.
One of the more difficult parts of writing standards for an information security program is getting a company-wide consensus on what standards need to be in place. This can be a time-consuming process but is vital to the success of your information security program.
- Used to indicate expected user behavior. For example, a consistent company email signature.
- Might specify what hardware and software solutions are available and supported.
- Compulsory and must be enforced to be effective (this also applies to policies).
Procedure
Procedures are detailed step-by-step instructions to achieve a given goal or mandate.
They are typically intended for internal departments and should adhere to strict change control processes. Procedures can be developed as you go. If this is the route your organization chooses to take it’s necessary to have comprehensive and consistent documentation of the procedures that you are developing.
- Often act as the “cookbook” for staff to consult to accomplish a repeatable process.
- Detailed enough and yet not too difficult that only a small group (or a single person) will understand.
- Installing operating systems, performing a system backup, granting access rights to a system, and setting up new user accounts are all examples of procedures.
Guideline
Guidelines are recommendations to users when specific standards do not apply.
Guidelines are designed to streamline certain processes according to what the best practices are. Guidelines, by nature, should open to interpretation and do not need to be followed to the letter.
- Are more general vs. specific rules.
- Provide flexibility for unforeseen circumstances.
- Should NOT be confused with formal policy statements.
Final Thoughts
As you can see, there is a difference between policies, procedures, standards, and guidelines. Each has their place and fills a specific need.
Policies are the data security anchor—use the others to build upon that foundation.
Keep in mind that building an information security program doesn’t happen overnight. It is a conscious, organization-wide, process that requires input from all levels. Building your program is not just up to the IT department; that’s where most of the issues come up.
Everyone needs to be on board.
Getting organization-wide agreement on policies, standards, procedures, and guidelines is further complicated by the day-to-day activities that need to go in order to run your business.
In the end, all of the time and effort that goes into developing your security measures within your program is worth it. Building a comprehensive information security program forces alignment between your business objectives and your security objectives and builds in controls to ensure that these objectives, which can sometimes be viewed as hindrances to one another, grow and succeed as one.
If you need help building your information security program—regardless of if it’s from square one or just to make top-end improvements—reach out to us at secureshieldbc.ca
* * * * * *
Author: Lyle Melnychuk
I am a 20 year information security veteran, and I tell it like I see it. I’m not known for being politically correct, and this sometimes gets me into trouble. More often than not; however, clients and colleagues come to appreciate the candor and common sense approach. If you look at security (the right way), you’ll find that it’s just not as complicated as people make it. I hope you enjoy my writings on security and other miscellaneous things. I really have a strong and deep passion for helping people with technology and making the world a better place.







